In the fight against fraud, the playing field is constantly changing. Fraudsters are now exploiting generative AI to industrialise phishing, create credible impersonations and automate attack scenarios. The result is a constant game of cat and mouse, where speed of adaptation makes all the difference. At Oneytrust, we have a simple belief: to counter AI-powered attackers, we must use AI better than fraudsters — without sacrificing customer experience or regulatory compliance.

What is triangular fraud?
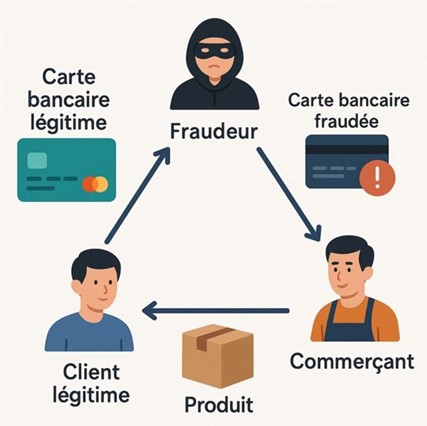
Triangular fraud is a complex and ingenious method of fraud that combines elements of real and synthetic identities to create a network of fraudulent transactions. This type of fraud relies on the interaction between three parties: the fraudster, the legitimate seller and the unwitting consumer, in order to divert resources discreetly and effectively.
How triangular fraud works:
The triangular fraud process can generally be broken down into four steps:
- Creation of multiple identities: fraudsters begin by creating synthetic identities by combining real and fictitious information from real customer information received during purchases on their website. This allows them to generate credible buyer profiles that can interact with sellers without arousing suspicion.
- Ordering products: using these identities, fraudsters place orders with legitimate sellers. Payment is often made with stolen or misused credit cards.
- Reshipping products: the purchased products are shipped to intermediate addresses or directly to the ‘real customer’ depending on the method used. At this stage, fraudsters may also sell the stolen products to real buyers via online platforms at a reduced price.
- Cash-out: Fraudsters cash out payments from genuine buyers, while the original seller remains unpaid or faces a chargeback.
Why is triangular fraud effective?
Triangular fraud is particularly effective because of its networked approach, which allows fraudsters to separate the elements of the transaction. The initial seller believes they are interacting with a legitimate buyer, while the final buyer thinks they are getting a product at a bargain price. This separation makes detection difficult, as individual transactions may appear legitimate because the information used is real, long-standing and sometimes even shows healthy activity. Traditional security rules are unable to detect these weak signals of fraud.
The MERLIN network
At Oneytrust, we are constantly detecting new fraudulent schemes. One of the most telling recent cases is that of a network we have named ‘Merlin’ because it used products from this brand to carry out its attacks. Detected in June 2024, this network perfectly illustrates the complexity and evolution of today’s threats.
It all started with an alert about unusual purchases: a sharp increase in orders for Merlin educational games, worth less than £100, from a partner specialising in childcare products. This sudden spike immediately caught our attention.
Our experts quickly spotted similarities between the orders, suggesting the existence of an organised network. However, certain elements were puzzling: the digital identities appeared reliable, and some profiles even belonged to real customers – but with a different email address. This was a clear sign of identity theft, which is rare for such small amounts.
To remove any doubt, we contacted the customers concerned. All confirmed their identity… but denied having made these purchases. The fraud was now certain. A thorough discussion with one of them revealed the key: he had indeed purchased the product, but on an online marketplace, not from our partner. The evidence provided enabled us to identify the fraudulent shop and understand the modus operandi: a triangular fraud.
Once the pattern had been established, our analysts listed the common signals associated with suspicious orders and created specific security rules. Thanks to these targeted actions, reinforced by direct checks with customers, we were able to block transactions linked to this network. The result: in less than 12 hours, the ‘Merlin’ network was neutralised.
This case shows how essential the responsiveness and expertise of our teams are in stopping new fraud networks as soon as they emerge. And the story of ‘Merlin’ is only just beginning… we will tell you more very soon.